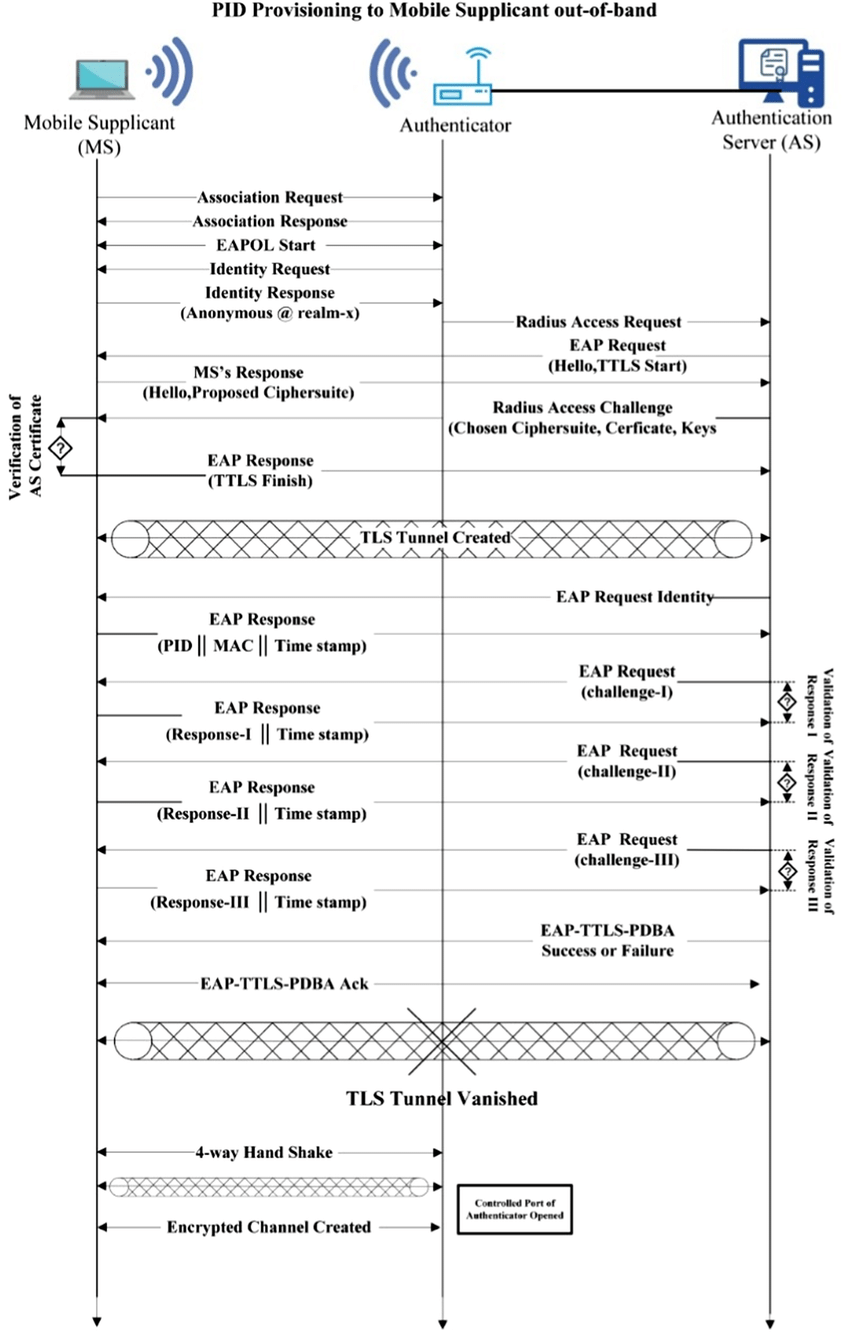
How EAP-TTLS works?
EAP-TTLS is a protocol that's used to provide secure authentication in wireless networks and point-to-point connections. It's an extension and improvement on EAP-TLS (Extensible Authentication Protocol - Transport Layer Security) and was created by Funk Software and Certicom. The protocol is often used in 802.1X (network access control) environments.
Here's how EAP-TTLS works:
- Initialization: First, the client (known as the supplicant in 802.1X terms) connects to the server (authenticator). The server presents its digital certificate to the client to prove its identity.
- Tunnel Creation: The client and server use the server's digital certificate to establish a secure encrypted tunnel between them. This is done by using the Transport Layer Security (TLS) protocol.
- Client Authentication: The client is then authenticated inside this secure tunnel. The specific method of authentication can vary – it might use a username and password, a certificate, or some other form of credentials. The key point here is that the authentication information is transmitted securely, within the encrypted tunnel, so it cannot be intercepted.
One of the advantages of EAP-TTLS is that only the server has to present a certificate during the initialization phase. The client can use simpler, less secure methods of authentication (like a password) within the secure tunnel. This makes EAP-TTLS more straightforward to implement on the client side than some other secure protocols, like EAP-TLS, which requires both the client and the server to present digital certificates to each other.
EAP-TTLS is widely supported and is used in a variety of network environments. However, its security depends on the strength of the server's digital certificate and the secure handling of the client's authentication credentials.
Diagram for the EAP-TTLS process:
- Supplicant (Client) ---> Authenticator (Server): The client sends a request to start an EAP-TTLS conversation with the server.
- Supplicant (Client) <--- Authenticator (Server): The server sends its digital certificate to the client.
- Supplicant (Client) ---> Authenticator (Server): The client validates the server's certificate, and both parties establish a secure TLS tunnel.
Inside the tunnel:
- Supplicant (Client) ---> Authenticator (Server): The client sends its authentication credentials (like a username and password) to the server inside the secure tunnel.
- Supplicant (Client) <--- Authenticator (Server): The server verifies the credentials and sends a success message back to the client if the credentials are valid.
- Supplicant (Client) ---> Authenticator (Server): Once the secure connection is confirmed, normal network traffic can now proceed.